Security without compromise
A new bar has been set for enterprise security. TrueVault is engineered to exacting standards that ensure data is truly private and safe.
Secure and scale everything
Warehouse and scale databases without the headaches. Easily move your operations to the cloud with limitless storage for anything that's critical to your business.
Store and search anything
Make life easy for dev teams by integrating TrueVault into your current application infrastructure without predefined formatting restrictions.
Compliant by default
Power applications with turnkey HIPAA compliance. The legal requirements of physical security and technical security are met or exceeded by TrueVault.
Risk managed by insurance
We back the integrity of our technology by protecting our customers under a comprehensive Privacy and Data Breach insurance policy.
TrueVault's Segmented Architecture Delivers TrueVault Redundancy and Security for Sensitive Data
1. API
The API subsystem securely handles all requests via HTTPS.
2A. Key
The Key Management subsystem stores encryption keys, initialization vectors, and HMAC keys for all records.
3. Data Store
The subsystem that stores encrypted BLOBs has no knowledge of what is being stored.
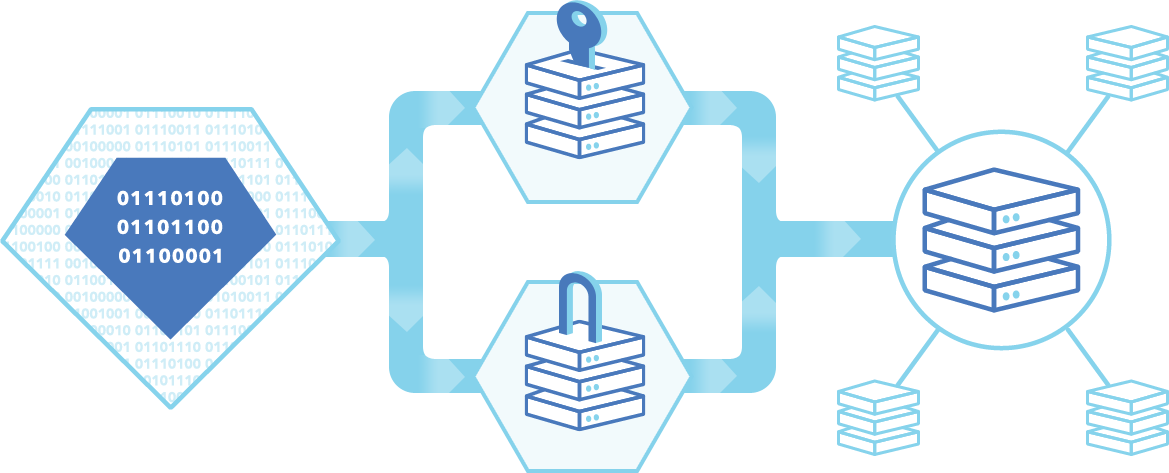
2B. Encryption
A completely independent subsystem handles all encryption and decryption.