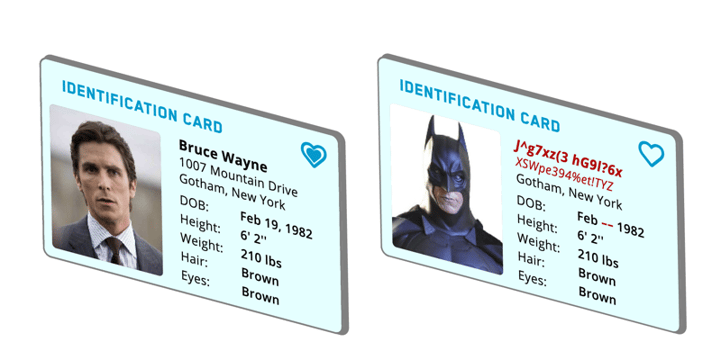
What happens after a data breach?
If your company aligns its data processing activities with the principles of privacy by design, the likelihood of a data breach happening is less than if you don’t adhere to these principles. However, in the event a data breach does occur, the penalties under the General Data Protection Regulation (GDPR or “The Regulation”) are harsh. In this fourth blog, we unpack the consequences facing businesses that experience a data breach.
Read More