Inside the Vault: Searching and Fetching Data
Virtually any business that works in the healthcare space will be accessing and managing health information. If personally identifiable information (PII) is linked with medical information, that data is considered protected health information (PHI), a special class of data that must be secured according to HIPAA standards. But building a HIPAA-compliant application requires expert knowledge in engineering for security as well as the law itself. There are few small businesses that have the financial and staffing capacity to build their own HIPAA-compliant solution from scratch, which is where TrueVault comes in.
TrueVault offers a HIPAA-compliant solution that integrates seamlessly into the architecture of your application. After reading our data flow series, you should have a solid understanding of how data flows between Vault, our flagship product, and your application, using TrueVault technology. This blog is the second and final part of our data flow series. Read part 1 of our data flow series if you haven’t already.
How It Works: Searching
When developers first start working with Vault, one of the first questions they will ask us is "how do I search for data stored in Vault?". The answer: Vault operates like any other database, but it’s more secure.
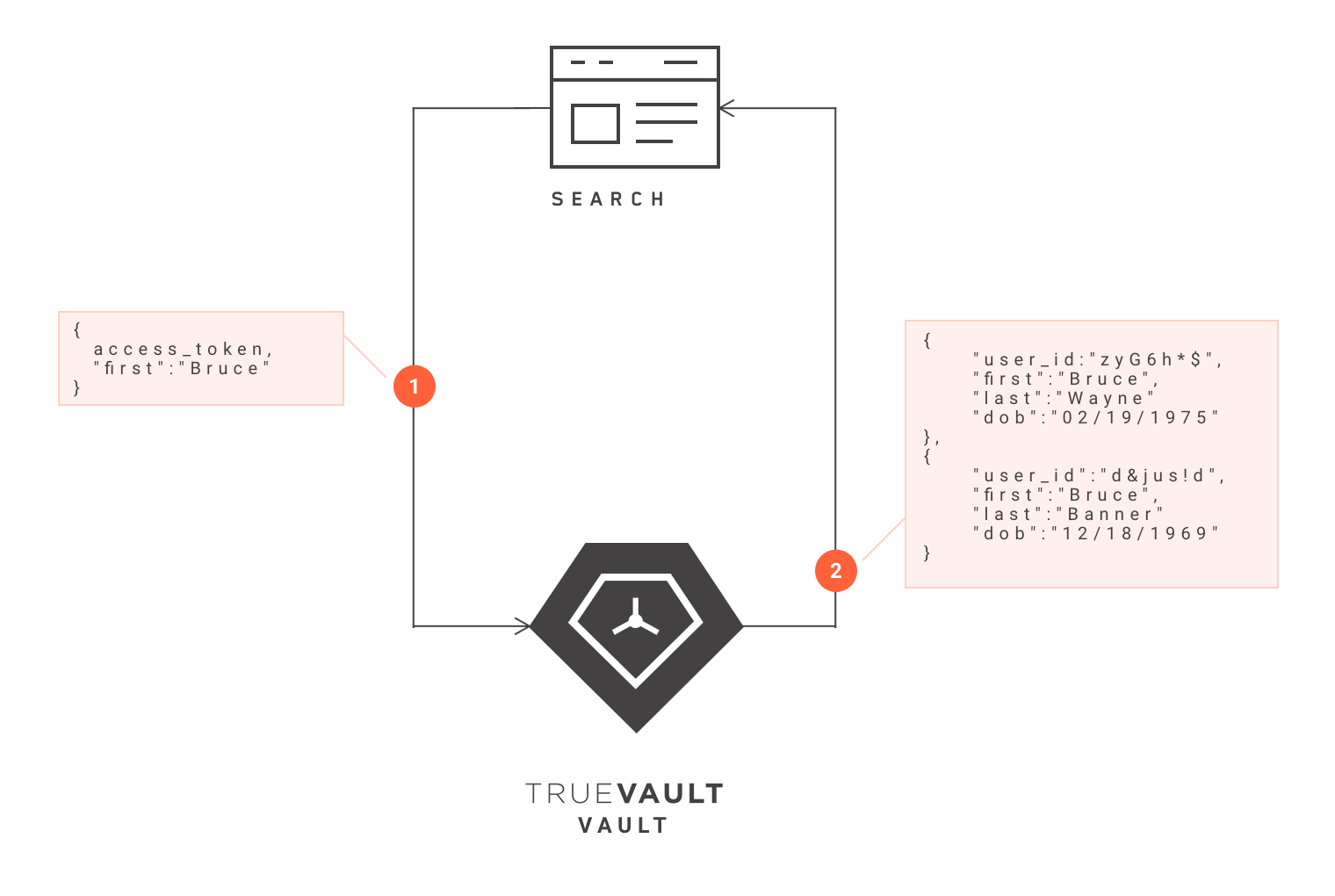
In practice, this means someone can query Vault, and Vault will return all records that match the query. For example, the end user, Amanda, needs to look-up someone’s record. Amanda starts by searching for "first name: Bruce" against the application, which is integrated with Vault. TrueVault receives the query and returns all records that match the criteria "first name: Bruce" so Amanda can select the specific record for the "Bruce" she was trying to find. The search function can be used to query any type of information that is stored in Vault.
The key takeaway is that to searching Vault isn’t a particularly novel or innovative feature, but its usefulness is rooted in its simplicity. Vault integrates seamlessly into other applications and is easy for your development team to implement and use. Your company can store data in Vault and search the data as you would any other database, except with Vault, your company stays HIPAA compliant.
Our HIPAA Compliant Checklist will give you the lowdown on how to bring your company to compliance using TrueVault.
How it works: Fetching
New TrueVault customers usually ask how they can retrieve a complete record. This question often comes up because TrueVault secures sensitive health data by de-identifying it using tokenization. By separating the identifying information (PII) from the health information (PHI), your company stays HIPAA compliant.
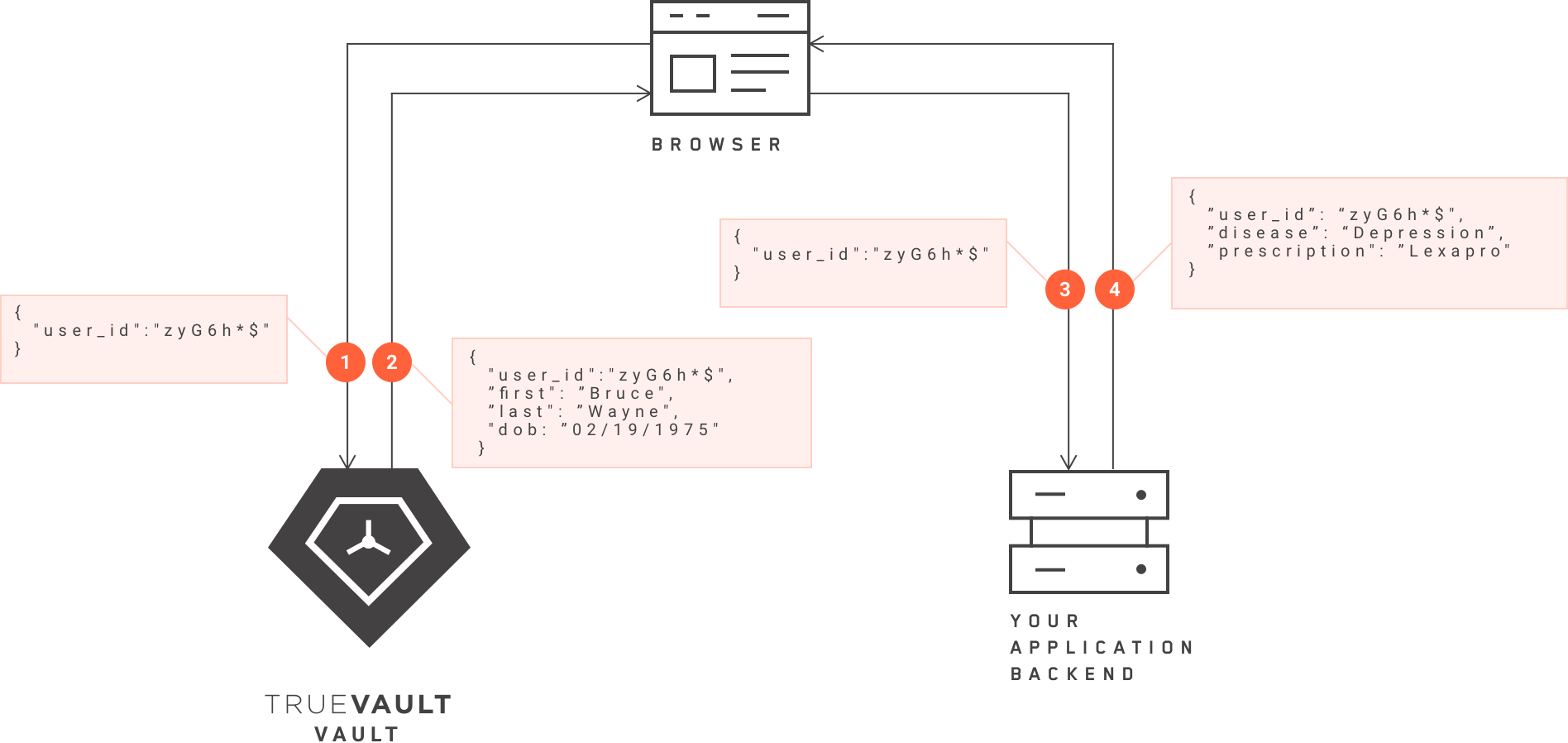
TrueVault requires an extra step (in the form of a second API call) when fetching a complete record because information that normally would be stored together (like name and medical information), is instead stored in different locations. Though decoupling the PHI components is what secures the data and keeps your company HIPAA compliant, it does add an extra step to the ‘fetching’ process.
In practice, this means that the application must make two API calls from the browser in order to fetch the complete record queried. For example, when the end user (Charley) queries the browser for the complete record, the browser will route the call to two locations (Vault and the application backend) that house the complete dataset that Charley requires.
One API call will send the TrueVault generated “user_id” to the Vault and retrieve the requested record stored in Vault. The second API call would also be made using the TrueVault generated “user_id” except this call would go to your own hosting provider to retrieve the other half of the record that is stored in your application backend The two returned records will meet in the browser, creating a complete record for Charley. Despite the extra step, Charley will experience no interruptions during the search.
The key takeaway is that data is stored in two different systems that are connected by a TrueVault-generated user_id. To retrieve both sets of information, TrueVault will make two API calls (one to Vault and your application) instead of a single API call to retrieve all relevant information associated with a user_id.
Read part 1 of our data flow series to learn more about how sensitive data moves between Vault and your application.
