Inside the Vault: How data flows in TrueVault
Virtually any business that works in the healthcare space will be accessing and managing health information. If personally identifiable information (PII) is linked with medical information, that data is considered protected health information (PHI), a special class of data that must be secured according to HIPAA standards. But building a HIPPA-compliant application requires expert knowledge in engineering for security as well as the law itself. There are few small businesses that have the financial and staffing capacity to build their own HIPAA-compliant solution from scratch, which is where TrueVault comes in.
TrueVault offers a HIPPA-compliant solution that integrates seamlessly into the architecture of your application. After reading our data flow series, you should have a solid understanding of how data flows between Vault, our flagship product, and your application, using TrueVault technology. This blog is part 1 of 2 in our data flow series.
How It Works: Authentication and Authorization
A core component to cybersecurity is access control. TrueVault helps your business manage which users can access sensitive data through a highly secure authentication and authorization process.
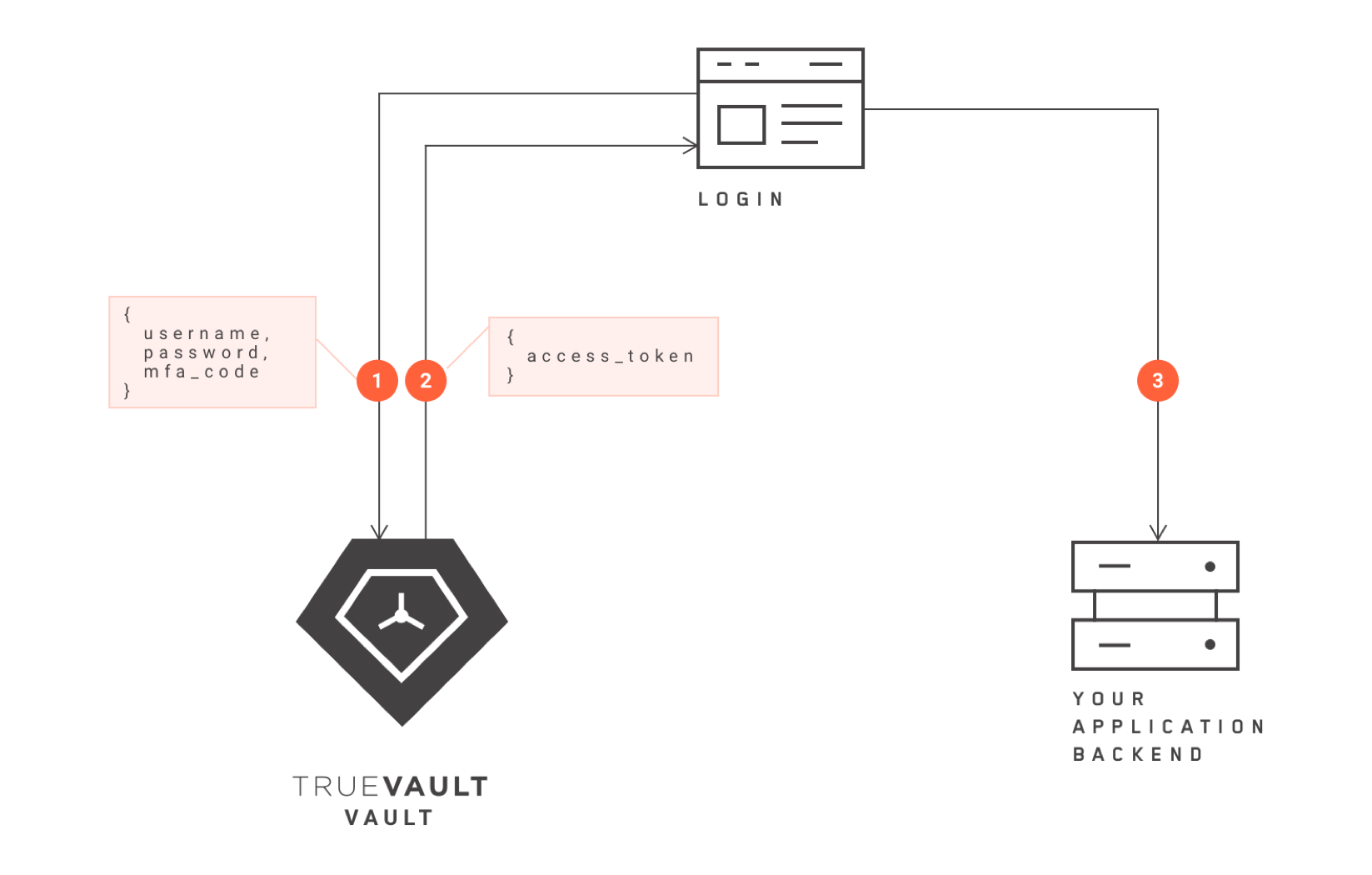
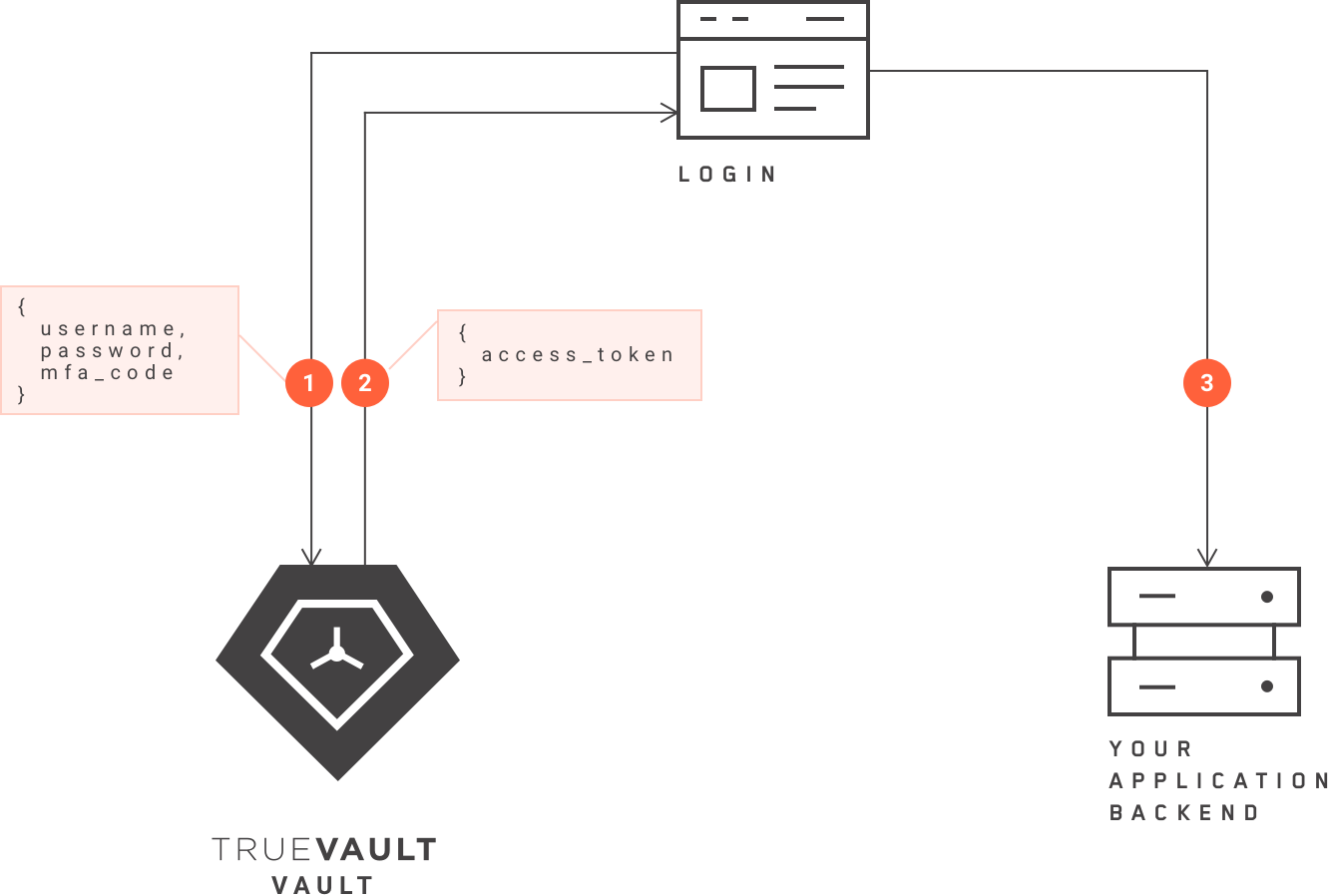
Every user on the platform must be authenticated before they can access data. Let’s assume User A opens the login page of your application’s browser to access their account. When User A submits their username and password, this information is sent to the back-end of TrueVault, where it is authenticated. The user experience is never interrupted during this process.
Once the login details reach Vault, Vault authenticates User A using the login details, and retrieves the appropriate access token. User A’s permissions are encoded in this access token. The access token is sent to the login page. User A is then granted access to the application according to the permissions articulated in the access token. This process is depicted above.
Storing Information in Vault
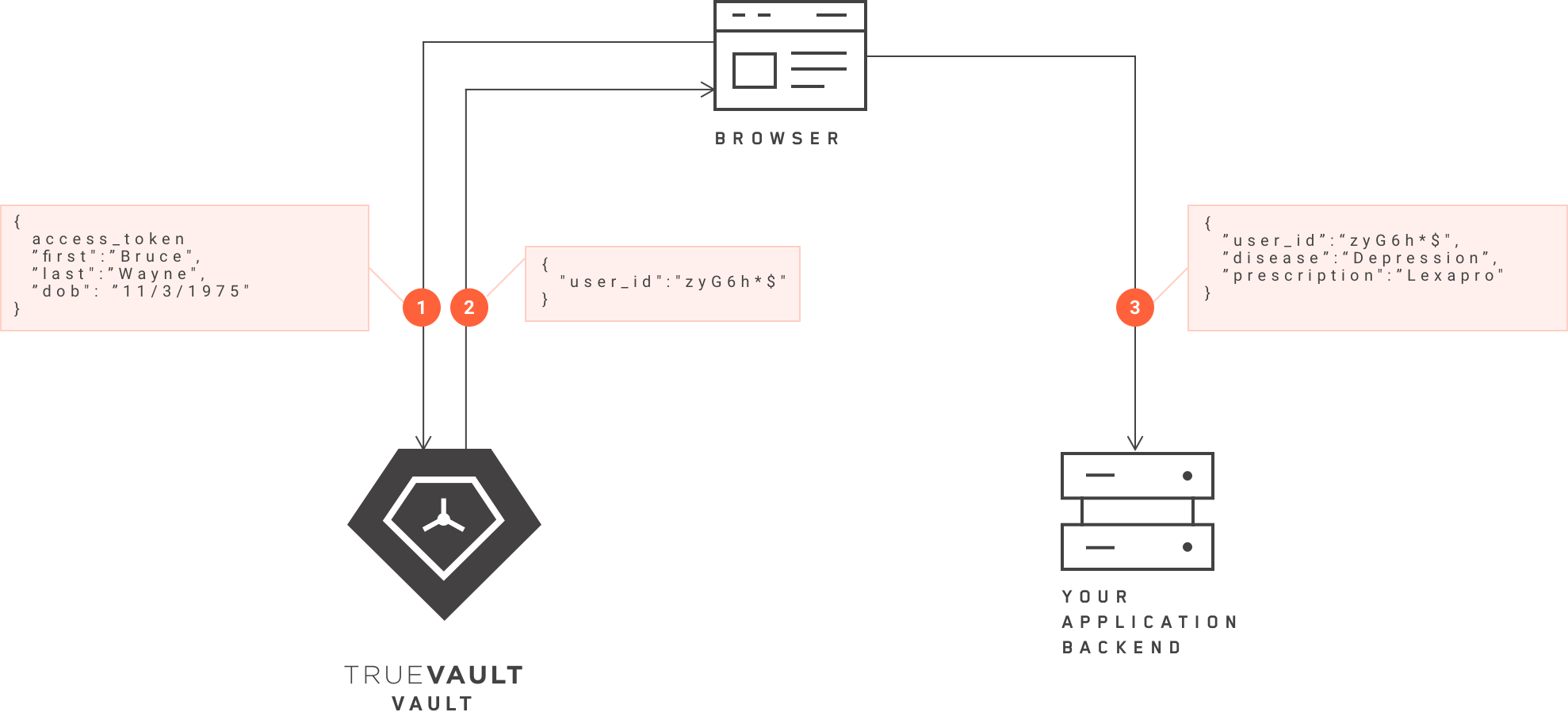
Since we specialize in HIPAA compliance, many of our customers are digital health enterprises. Oftentimes, these health enterprises achieve HIPAA compliance through data de-identification. This is achieved by separating the PII from the medical information, with the PII stored in Vault, and the medical information stored in the enterprise’s application back-end, which is itself stored in the hosting solution (e.g., Amazon Web Services, Azure etc.). A hypothetical example of how PHI is securely stored is explained below.
Bruce Wayne, or his doctor enters: first name, last name, birthday, depression, and Lexapro (Wayne’s medication) into the browser. Next, the PII and medical information is decoupled. PII (name, birthdate) is sent to Vault and the medical information (depression, Lexapro) is sent to their application back-end. The PII remains stored in Vault, but a de-identified User ID is sent back to the browser. The application reads the User ID. Finally, the non-PII medical information and de-identified User ID is stored in the application.
This method is used time and again because it allows a digital health enterprise to circumvent HIPAA by de-identifying sensitive data and enhancing security using Vault. By decoupling PII from medical information, and then storing de-identifying the data is de-risked and HIPAA protocols no longer apply.
In part 2 of our blog post, we introduce two other functions of Vault and how TrueVault’s 10 Layers of Security guarantees compliance and enhanced security.